Sybil Attack
Detecting Sybil attacks in blockchain networks faces many challenges. Here's what I've discovered.
Hello! Kevin Wang here. I'm a devoted product manager by day, but come evening, I'm the force behind a Gen-AI Tool - tulsk.io. My mission? To fuel your venture, guide you through the startup world, spotlighting user experience, product management, and growth strategies, particularly in the web3 and AI spaces. Keen to dive deeper? Join the tulsk.io community. Your support is invaluable and ensures I can share insights for budding entrepreneurs like you. Let's journey together!
Incentivizing users is crucial in any community to ensure sustainable operations. In the blockchain-backed Web3 communities, celebrated for their transparency and security, airdrops have become a popular way to distribute capital and power. However, the safe use of airdrops as incentives and tools for empowering decentralized governance remains a topic of ongoing debate.
Startups in the decentralized applications (DApps) sphere often use airdrops as a reward mechanism for early adopters, granting free tokens. This approach, however, can attract hackers, known as Sybils, who create multiple accounts to increase their gains. Qualification for these airdrops typically involves interaction with the DApps. These interactions, recorded as transactions on public blockchains, could potentially expose patterns that signify the presence of accounts under Sybil's control, revealing similar behavioral signatures.
Here are some questions you might be curious about
What is a Sybil Attack?
How are Sybil attacks detected in DApps?
What is the proposed framework for detecting Sybil’s accounts?
What challenges exist in detecting Sybil attacks in blockchain networks?
What future developments are expected in combating Sybil attacks?
What is a Sybil Attack?
A Sybil attack involves a single entity creating multiple fake identities (accounts) in a network. In the context of blockchain and DApps, it often refers to creating multiple accounts to unfairly benefit from activities like airdrops.
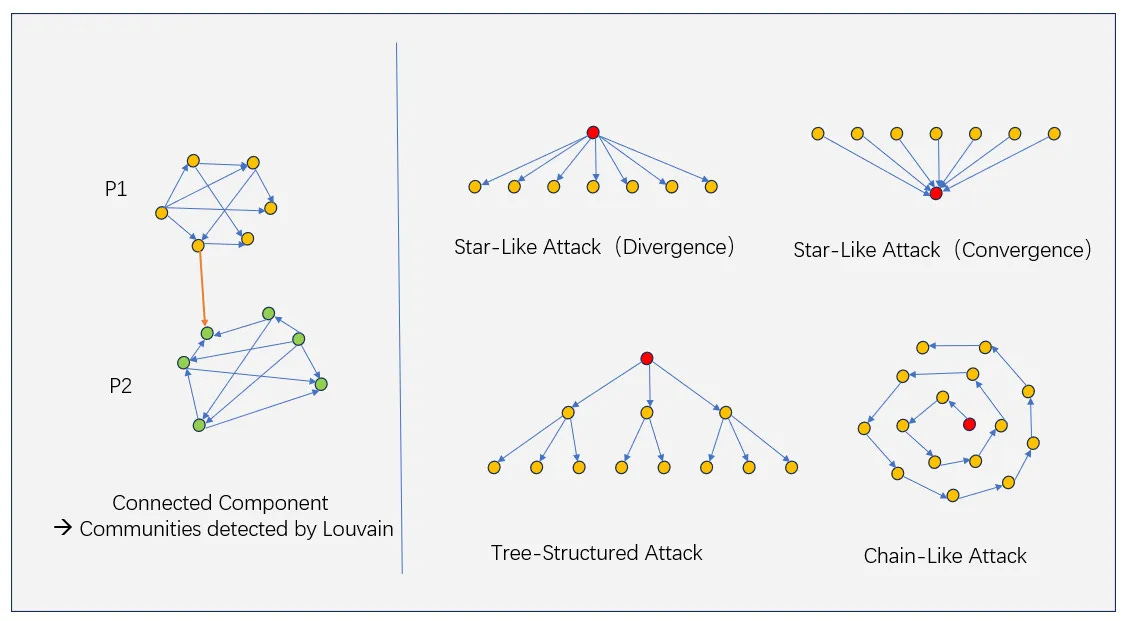
Sybil clusters are identifiable based on known attack patterns, as illustrated in the diagram:
Star-Like Divergence Attacks: This involves addresses being funded by a single source, creating a star-like pattern in fund distribution.
Star-Like Convergence Attacks: In this pattern, multiple addresses send funds to a single target, forming a converging star-like structure.
Tree-Structured Attacks: Funds are distributed in a tree topology, branching out from a central point.
Chain-Like Attacks: This involves sequential fund transfers from one address to another in a linear chain topology.
How are Sybil attacks detected in DApps?
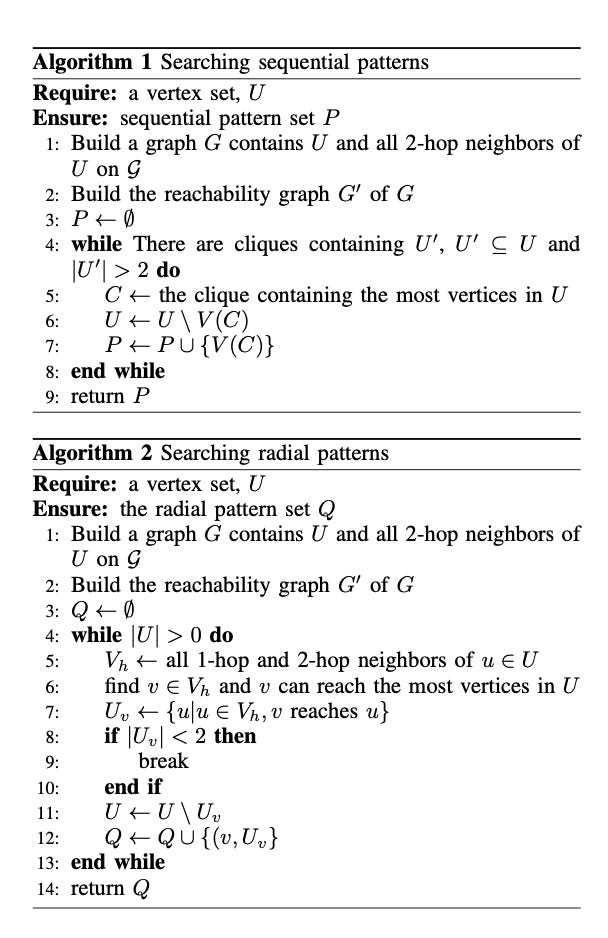
Two fundamental and regular token transfer patterns are identified:
Sequential Pattern Model: In this approach, a bot distributes tokens from a central treasury account to the first controlled account. This account then interacts with a DApp. After these interactions, any remaining tokens are transferred to the next account in the sequence, perpetuating the cycle.
Radial Pattern Model: In this model, the bot simultaneously sends tokens from a treasury account to all controlled accounts. Each of these accounts independently engages with the DApp. Subsequently, the remaining tokens might either be re-collected or left within the accounts to emulate the behavior of ordinary users.
What is the proposed framework for detecting Sybil’s accounts?
The framework starts with gathering transactions related to Sybils, followed by constructing a transaction graph, identifying connected components, generating activity sequences for each vertex, and implementing clustering algorithms. The sequential and radial token transfer patterns are then explored using these algorithms, aiding in the identification of Sybil-controlled accounts.
What challenges exist in detecting Sybil attacks in blockchain networks?
Detecting Sybil attacks in blockchain networks faces key challenges:
Complex Transaction Patterns: Transactions from Centralized Exchanges (CEX) to numerous accounts create intricate patterns, complicating detection efforts.
Limited Interaction Diversity: Similar behaviors across nodes can lead to misidentifying legitimate accounts as fraudulent, suggesting a need for diverse interactions with different decentralized applications (DApps).
Ambiguity in Detection: The subtle nature of these attacks limits the effectiveness of traditional supervised learning, requiring a mix of machine learning and human review.
Data Analysis Challenges: A community-driven approach is essential for identifying Sybil accounts, involving anonymized data and open-source tools for model development.
Difficulty in Identifying Fake Identities: Sophisticated strategies used by attackers to mimic real users add to the complexity of accurately identifying fraudulent accounts.
What future developments are expected in combating Sybil attacks?
Increasing the cost of creating an identity: Making it more expensive to run a node or create a new account can discourage attackers from launching Sybil attacks
Verifying trust before joining a network: Implementing reputation systems where only verified users can invite new users can help prevent Sybil attacks
Using a combination of machine learning and human review processes: This approach can help improve the accuracy and efficiency of Sybil detection
Developing decentralized governance mechanisms: Many blockchain networks employ decentralized governance mechanisms where decisions are made collectively by the network's participants, reducing the impact of individual Sybil attackers
Conclusion
In the Web3 and blockchain realm, addressing Sybil attacks—where multiple fake identities are created for unfair gains, especially in DApps and airdrops—is crucial. Detecting these attacks involves complex pattern analysis and combines machine learning with human insights. Future solutions include making identity creation costlier, employing reputation-based access, and enhancing decentralized governance to ensure the security and integrity of these digital communities.
For a deeper understanding, it's beneficial to delve into the paper "Fighting Sybils in Airdrops" and explore resources like the "Airdrop-Sybil-Identification" on GitHub.
Related Readings:
Unpacking Creators’ Practices with Non-Fungible Tokens (NFTs) and Their Communities
The impact of NFT profile pictures within social network communities
Altruistic and Profit-oriented: Making Sense of Roles in Web3 Community from Airdrop Perspective
🌟 Spread the Curiosity! 🌟
Enjoyed "Curiosity Ashes"? Help ignite a wave of innovation and discovery by sharing this publication with your network. Let's foster a community where knowledge is celebrated and shared. Hit the share button now!